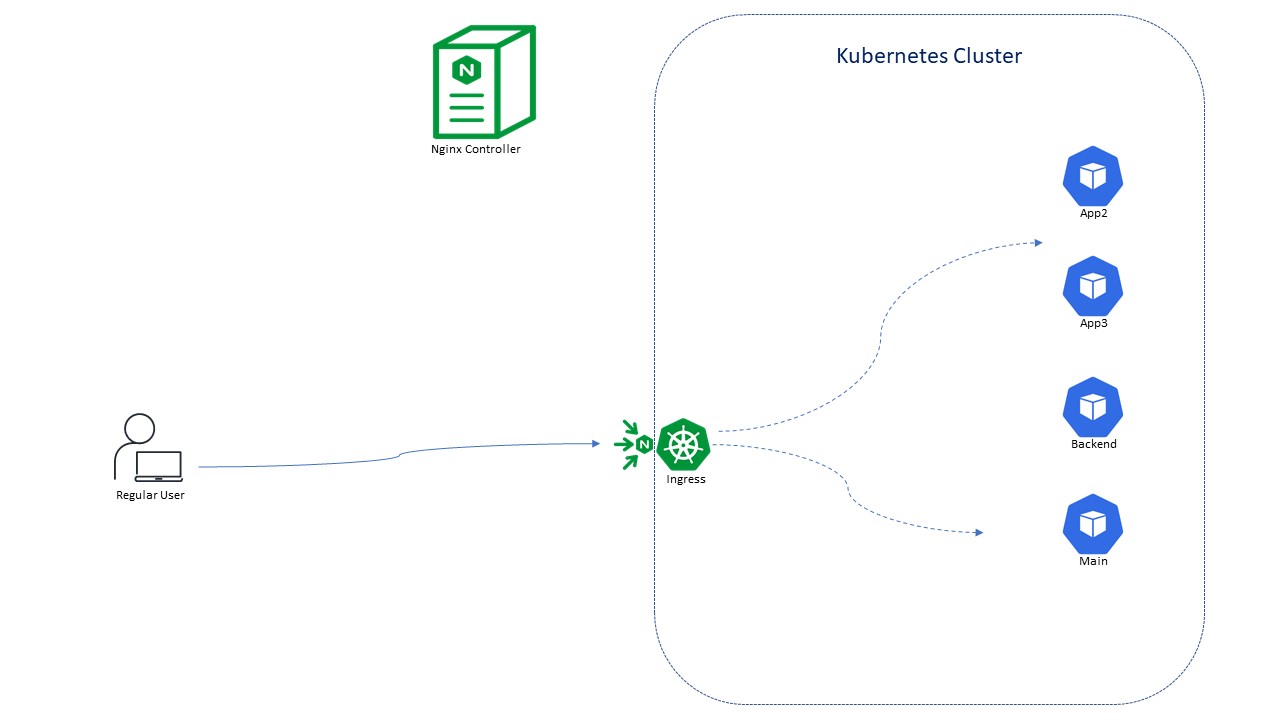
Mutual TLS
Enabling MTLS on our Nginx Ingress Controller is quite simple, we are going to add two lines to the existing config.
- We are going to add the bellow directives to our Ingress configuration, This will enable MTLS while using the pre uploaded ca.pem certificate.
ssl_client_certificate /etc/ssl/mycerts/ca.pem;
ssl_verify_client on;
Apply the new configuration:
cat << EOF | kubectl apply -f -
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: arcadia
annotations:
nginx.com/health-checks: "true"
ingress.kubernetes.io/ssl-redirect: "true"
nginx.com/sticky-cookie-services: "serviceName=arcadia-main srv_id expires=1h path=/"
nginx.org/server-snippets: |
proxy_ignore_headers X-Accel-Expires Expires Cache-Control;
proxy_cache_valid any 30s;
ssl_client_certificate /etc/ssl/mycerts/ca.pem;
ssl_verify_client on;
nginx.org/location-snippets: |
proxy_cache my_cache;
add_header X-Cache-Status \$upstream_cache_status;
spec:
tls:
- hosts:
- $nginx_ingress
secretName: arcadia-tls
rules:
- host: $nginx_ingress
http:
paths:
- path: /
backend:
serviceName: arcadia-main
servicePort: 80
- path: /api/
backend:
serviceName: arcadia-app2
servicePort: 80
- path: /app3/
backend:
serviceName: arcadia-app3
servicePort: 80
EOF
Browse to the Arcadia site again, and you’ll see that you can’t access it since you don’t have the client certificate.
Verify this is actually working by running the bellow command, it will use the client cert/key pair on the Cloud9 instance to authenticate:
curl -v -k \
--key certs_for_mtls/01-alice.key \
--cert certs_for_mtls/01-alice.pem \
https://$nginx_ingress/ \
| grep 'Welcome'
- We are finished with this part of our experience and achieved the bellow environment.
Before moving forward reapply the ingress configuration without the two lines we just added.
cat << EOF | kubectl apply -f -
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: arcadia
annotations:
nginx.com/health-checks: "true"
ingress.kubernetes.io/ssl-redirect: "true"
nginx.com/sticky-cookie-services: "serviceName=arcadia-main srv_id expires=1h path=/"
nginx.org/server-snippets: |
proxy_ignore_headers X-Accel-Expires Expires Cache-Control;
proxy_cache_valid any 30s;
nginx.org/location-snippets: |
proxy_cache my_cache;
add_header X-Cache-Status \$upstream_cache_status;
spec:
tls:
- hosts:
- $nginx_ingress
secretName: arcadia-tls
rules:
- host: $nginx_ingress
http:
paths:
- path: /
backend:
serviceName: arcadia-main
servicePort: 80
- path: /api/
backend:
serviceName: arcadia-app2
servicePort: 80
- path: /app3/
backend:
serviceName: arcadia-app3
servicePort: 80
EOF